CyberSuite stores given source code in a dedicated and encrypted bucket in S3.
Cybershell takes security very seriously. CyberSuite is S2 compliant and AWS is SOC-2 compliant and AWS advanced Technology Partner. Cybershell keeps your code encrypted in compliance with the industry best practices.
Following are the flow of code submission of cybershell users and how cybershell keeps user code and secure it. Here is the diagram which clearly describe the user code submission steps:
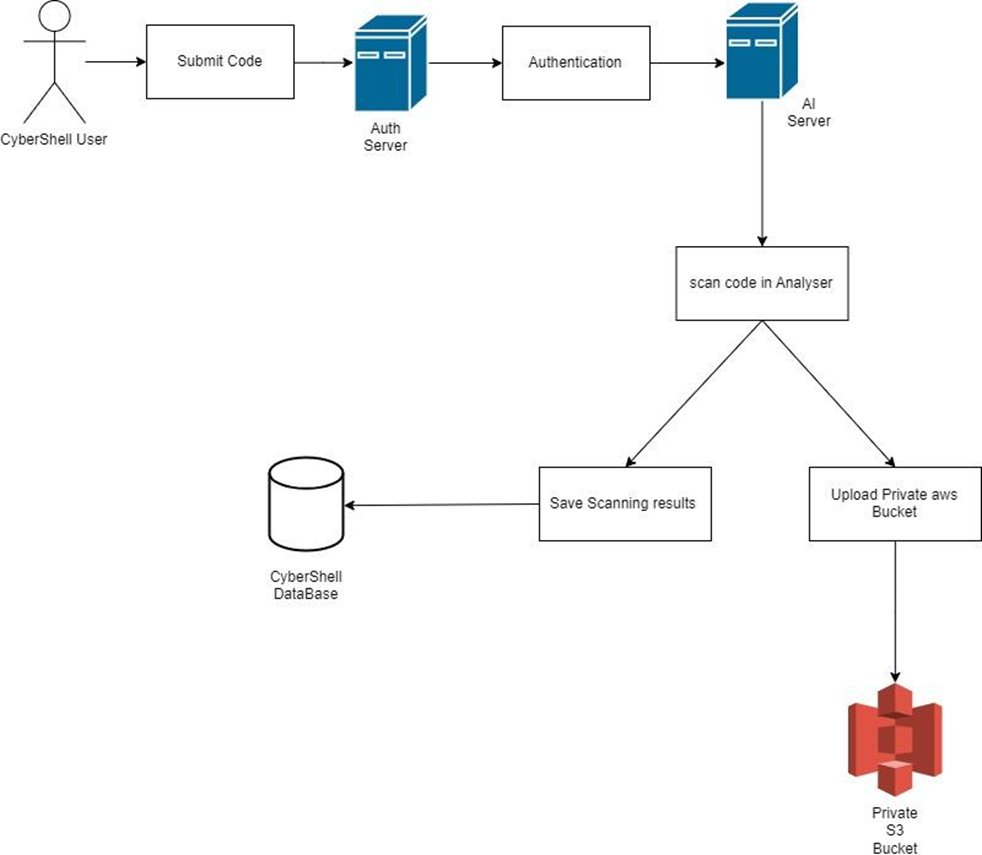
Step1:
Firstly, A Cybershell user logged in to the portal and submitted their code file which is a single or zip file in the case of multiple files.
Step2:
Then the user request goes to Cybershell Auth server which authenticates the user from different layers and identifies him/her. If authentication fails then the request stops and sends it back to the user with an authorization message, if the request succeeds then it moves forward to the next step.
Step3:
Cybershell AI Server gets the user code after authorization and passes it to AI Analysers and analyses the code with different trained models.
Step4:
After analysis, Cybershell AI server saves the user code to AWS private bucket, which is highly secured with AWS recommended security layers.
Step5:
At the same time, Cybershell AI server saves the Analysis results to the secure Cybershell Database.
We can easily understand that Cybershell security layers are highly secured, and its user code is completely safe and secure.
Cybershell provides you with all the list of sessions in your organisation account. And this is done by a superuser account.
